Docker
Running the core of your application in a compliant Docker environment.
When you create the first node in a cluster, MedStack Control automatically initializes the Docker environment.
MedStack Control runs your Docker applications using the Docker Swarm orchestration layer. The first node in the cluster is configured as the Swarm manager by default. You can change the manager node at any time by promoting a node to manager once there are worker nodes added to the cluster.
Capabilities and limitations
Please take a moment to familiarize yourself with the capabilities and limitations of Docker on MedStack Control.
Security
Backup and restore
The Docker environment is a MedStack managed resource. An agent on the host machine ensures a Docker environment snapshot is captured every hour.
- We preserve these snapshots for 24 hours.
- Every day for 1 week we preserve the final day's snapshot.
- Every week for 1 month we preserve the final week's snapshot.
- Additionally, we preserve the final month's snapshot indefinitely as long as you have an active MedStack Control subscription.
Generating evidence and backup validation
A list of Docker volume backups can be reviewed and exported for validation and evidence generation.
Restoring a backup
Docker volume backups can be restored to nodes using the restore volume feature.
Inclusions
Backups of the Docker environment contain:
- Secrets
- Configs
- Registries
- Services
- Volume mappings
- Disk data stored in Docker volumes
Exclusions
There are some notable exclusions of the backups to note:
- Disk data that is not stored in Docker volumes (for example, anonymous volumes)
- The number and size of nodes operating in the cluster
- Static IP addresses mapped to nodes
Networking
An encrypted internal overlay network is automatically created when you create the Docker environment. By default this network is only accessible between the other containers in the Docker environment and the resources within the same cluster.
Ingress
Inbound connections to services in the Docker environment proxy through MedStack Control's load balancer service and are limited to HTTPS only. To enforce encryption in transit, HTTP requests are automatically upgraded to HTTPS by the load balancer.
When a container opens a port using the normal technique (defined in a Dockerfile), the port is accessible on the overlay network but not from the internet. When configuring a service for deployment to Docker on MedStack Control, the domain mapping section of the service configuration form lets you define the services and at which domains they can receive connections from the internet. This is all proxied through the load balancer service.
Only incoming HTTPS connections are supported. HTTP requests are automatically redirected to HTTPS.
Egress
Outbound connections from the Docker environment can be done over any protocol. Although most outbound traffic from services is delivered through HTTPS, some common protocols for outbound file transfer include SFTP, SC, and rsync.
In the next section, we'll start with deploying the load balancer service followed by the other Docker services your application depends on.
Actions
Create
To create a Docker environment in a cluster, simply create at least one node. As long as there is a node in the cluster, a Docker environment will exist.
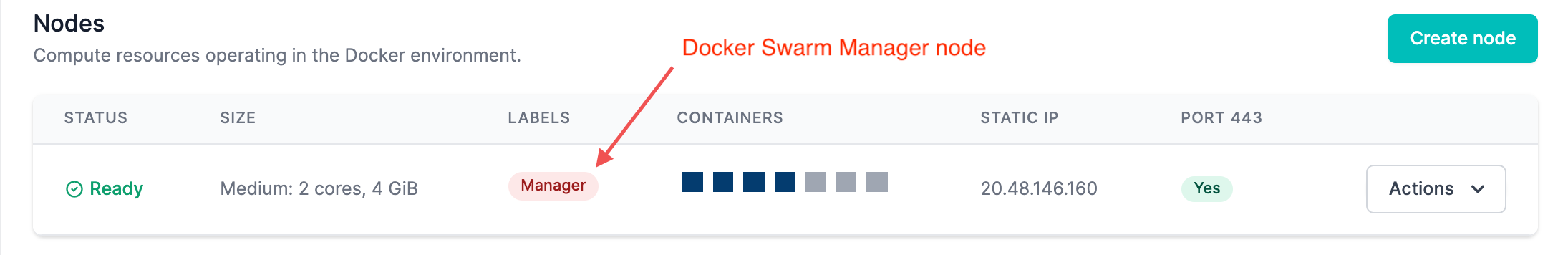
The Swarm Manager node is labeled and orchestrates the Docker environment.
Manage Docker
The Docker configuration can be managed by clicking the Manage Docker button in a cluster.
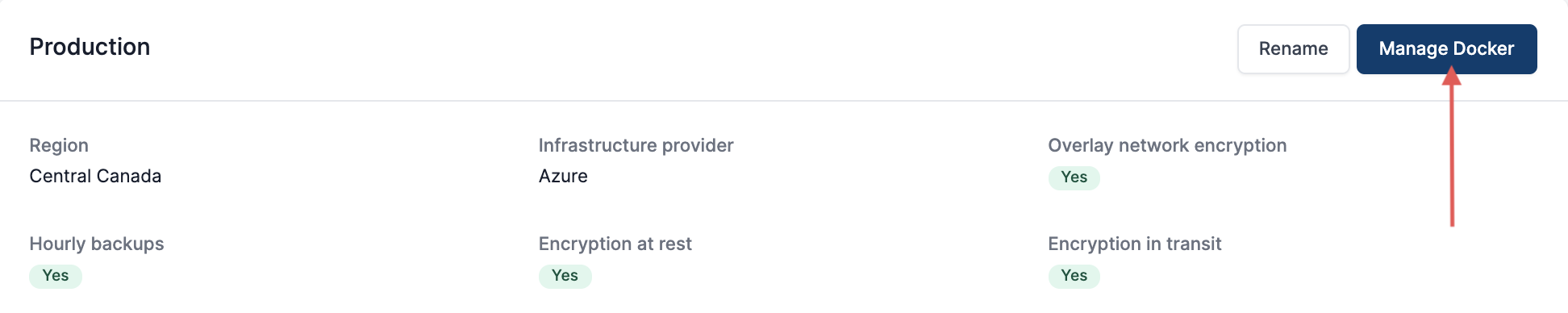
This is explored deeply in the Docker configuration article in the Deploy section of this guide.
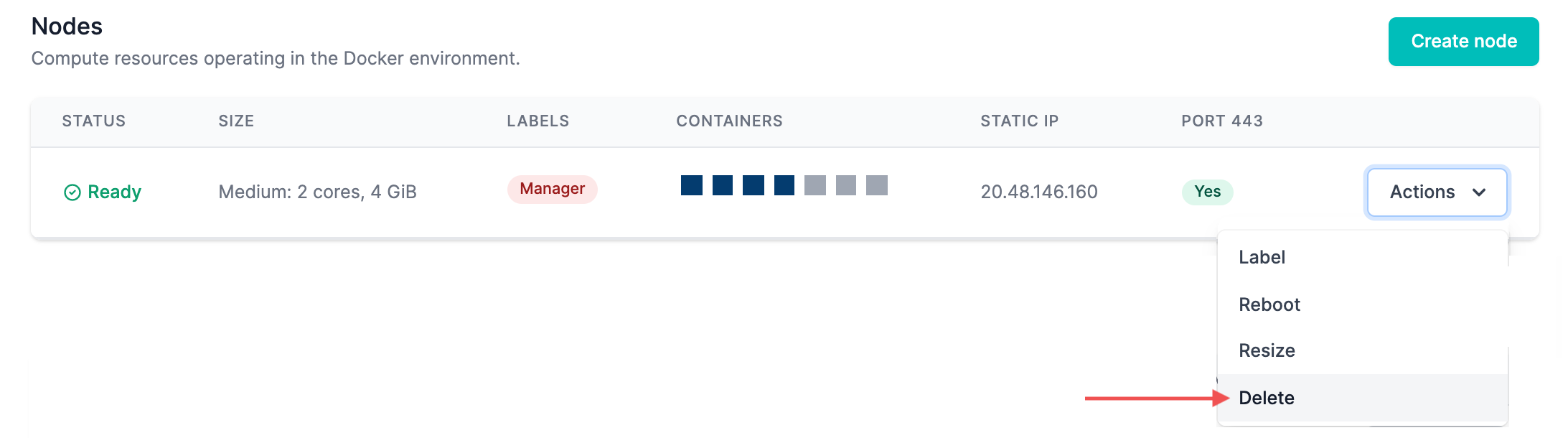
Delete
To delete a Docker environment in a cluster, simply delete all nodes. It's important to note that the most recent hourly snapshot will retain the configuration of the Docker network as specified in MedStack Control's backup and restore system.
Updated about 1 year ago
Now that the Docker environment has been initialized, you can prepare to deploy your application and services.
